Outside the IT Department, IT security is regarded in an entirely fallacious way: as a super expensive insurance policy that only adds actual value when things go wrong. However, those who work with this daily are well aware that this certainly also depends on investments that help ensure items do not go wrong.
Now is the worst possible moment to neglect your company’s IT security.
And we are well aware that it could ALWAYS be exhausting to be asked questions like:
- Do you have your IT security covered?
- Is everything up to date?
- Can we sleep soundly at night?
If you work in an IT Department, you are well aware of the importance of protecting the company you are part of. And this is why you toil, fight for investments, and implement policies that can be perceived by many as restrictive. However, you know too well that investments in IT security are perceived somewhat erroneously as insurance investments that only add real value when things go wrong. However, many forget that well-functioning IT security is undoubtedly ALSO the insurance that helps prevent items from going wrong.
Over time, vicious external attacks against data and infrastructure have become more numerous and creative and come from many different fronts.
It was pretty recently that the Government’s National Cyber Security Strategy also emphasized that 40 percent of all small and medium-sized enterprises in Denmark have an inadequate level of digital security and that 46% of the country’s IT systems are critical to society in lousy condition.
Therefore, it is necessary to get the essential things right.
Do not skip IT security
So what is the essential thing when we talk about IT security?
We have paid a visit to www.sikkerdigital.dk, where the Danish Agency for Digital Government and the Danish Business Authority has gathered necessary information security knowledge. At the same time, we have consulted CapaSystems’ System Administrator, Christian Wadskov, who is very focused on continuously ensuring that we as a company take external threats seriously at all times.
“It is my clear stance that given the level of threat we currently face, all companies should look over their shoulders and keep trying to be one step ahead of intruders. Failing this, things can go wrong. At my company, I am constantly plugging holes and making tweaks. And I would be lying to you now if I were to say that my colleagues do not confront me about this, as they certainly have the right to be irritated about having to change their working methods and working under restrictions. But this is just how it is — and they also understand this well every time I push them,” says System Administrator Christian Wadskov, CapaSystems.
Seven pieces of advice on IT security
sikkerdigital. dk has put together seven pieces of advice on IT security (in Danish) for small and medium-sized companies that have not implemented the essential IT security measures:
- Update your programs continuously
- Purchase an antivirus and firewall
- Back up your data
- Learn to spot suspicious emails
- Come up with strong passwords
- Give your IT provider security requirements
“There is nothing wrong with this advice. The objective is to help small enterprises gear up against cyber attacks and adopt more secure digital behavior. But in my world, this advice does not come even close to being enough. Where on the list is Multi-factor authentication or management of local administrator rights for company employees? This is the bare minimum that should be added to the list,” continues Christian Wadskov.
There is nothing foolish about minimum requirements
Another thing noted on www.sikkerdigital.dk is that the Danish Agency for Digital Government and the Danish Business Authority has cataloged the 20 minimum technical requirements that ALL state authorities must comply with by 1 January 2023.
“They are on the right side of things here. There is nothing foolish about minimum requirements, and I think that all companies of a certain size should look at this list as it provides them with good protection. And not being a “state authority” means you will not have that strict deadline hanging over your head. However, I would recommend that you not wait long to go through the list and identify if there are areas where you can tighten up your IT security,” concludes Christian Wadskov.
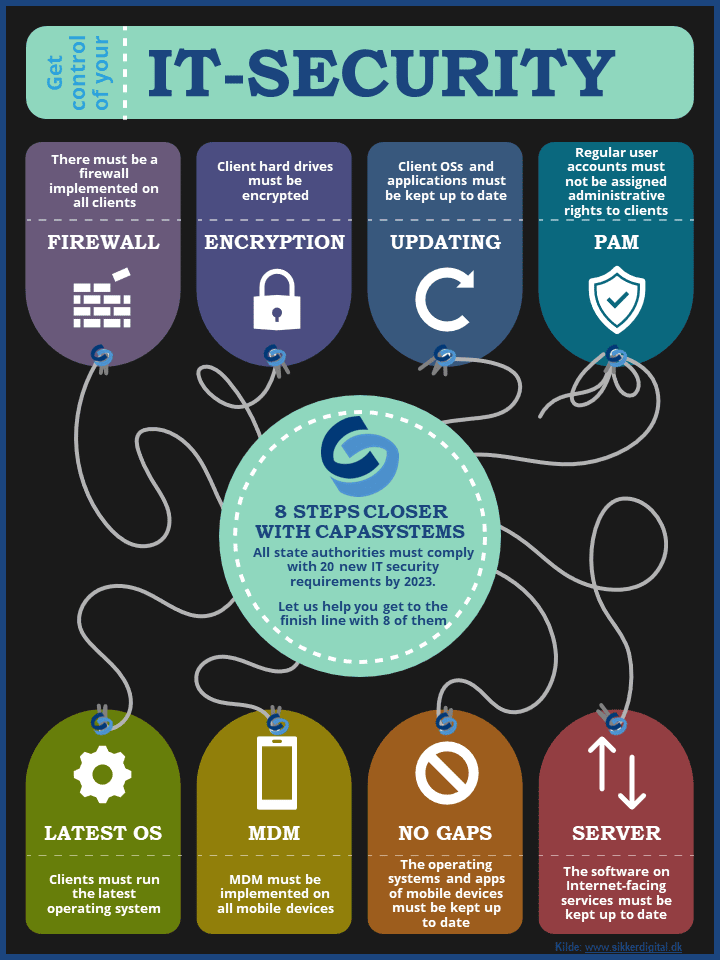
The Chief Product Officer of CapaSystems, Martin Søndergaard, has also gone through the list to take stock of what CapaSystems could help with:
“The way I see it, we can help you to the finish line with 8 out of these 20 minimum requirements. And the good thing is that we can do it with simple and intuitive solutions that do not require much after-sales consulting and that have been developed by a Danish software company with expertise in these areas.